Introduction
The number of challenges that organizations are facing in cyberspace is increasing day by day. Conducting cyberattack simulations and cyber drills is no longer optional; it’s a strategic necessity.
In this article, we explain why these exercises matter, how they support measurable outcomes, and how platforms like Simulations Labs make running realistic, effective simulations easy through CTF hosting, cybersecurity simulations, cyber drills, and cyber ranges.
What are cyberattack simulations and cyber drills?
Cyberattack simulations recreate realistic threat scenarios so teams can practice detection, response, and recovery in a controlled environment.
Cyber drills are structured exercises that evaluate an organization’s incident response plans and the people who execute them.
Common formats include tabletop exercises, live incident simulations, red-team/blue-team exercises, and Capture The Flag (CTF) competitions. Each format delivers different benefits, from incident response coordination to hands-on technical skill development.
Top benefits of running cyber simulations and drills
- Identify gaps in people, process, and technology.
Simulations expose weaknesses in your security stack and incident response procedures. They show where staff lack training, where processes are ambiguous, and where tooling fails to deliver the expected visibility or control.
- Improve response times and decision-making under pressure.
Practicing in realistic conditions reduces hesitation and confusion during real incidents. Teams that have drilled together move faster, follow playbooks more effectively, and limit business impact.
- Validate incident response plans and communication paths.
Drills surface gaps in escalation paths, communication protocols, and stakeholder coordination (IT, legal, communications, executive leadership). The result: clearer roles, faster approvals, and better cross-functional collaboration during emergencies.
- Strengthen practical cybersecurity skills.
Hands-on exercises, especially CTF-style labs and cyber ranges, let practitioners develop critical skills: malware analysis, forensics, threat hunting, vulnerability exploitation, and remediation. These skills are hard to teach in theory but easy to improve with realistic practice.
- Test and tune detection and prevention tools.
By simulating attacks, you can validate that SIEM alerts, EDR detections, and network monitoring behave as expected. You’ll also identify tuning opportunities to reduce false positives and improve signal-to-noise ratio.
- Demonstrate compliance and readiness to stakeholders.
Regulators, customers, and board members increasingly expect evidence of cyber readiness. Simulations provide auditable proof that you tested controls, practised responses, and improved over time.
Why CTF hosting and cyber ranges are particularly effective
Capture The Flag (CTF) competitions and cyber ranges offer immersive, hands-on environments tailored for learning and assessment. They recreate systems, misconfigurations, and attack paths so defenders experience real-world tactics, techniques, and procedures (TTPs).
Benefits of CTF hosting and cyber ranges:
- Scalable training: run events for small teams or large cohorts without complex setup.
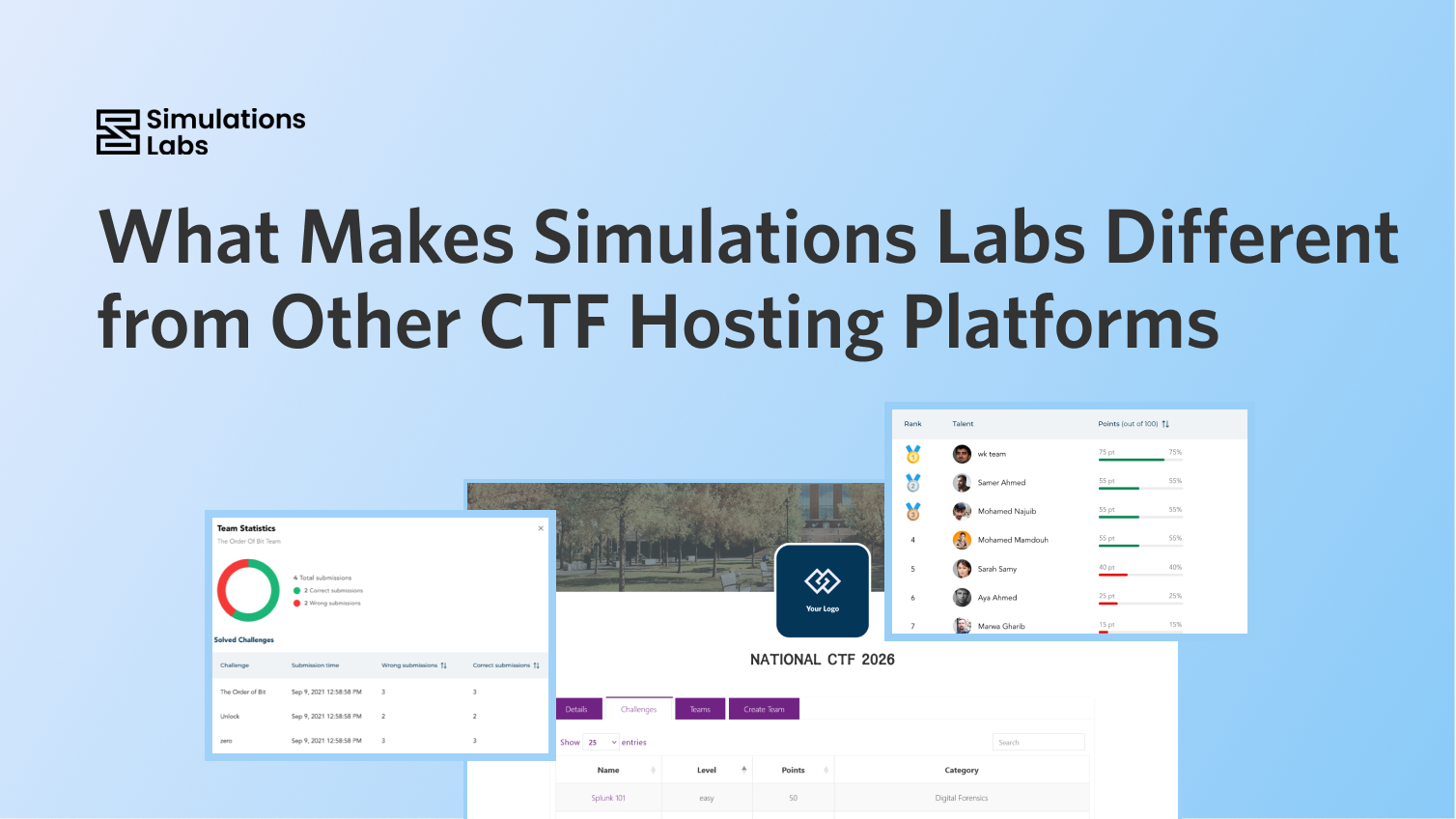
- Measurable outcomes: leaderboards and analytics let you quantify performance and progress.
- Customizable scenarios: tailor content to your tech stack, industry threats, or learning objectives.
- Fair and secure assessment: features like dynamic flags prevent cheating and ensure reliable results.
Use cases: who should run simulations?
- Enterprises and SMBs:
For team readiness and incident preparedness. Many companies run internal cyber drills to validate IR plans and train SOC staff.
- HR and Talent teams:
To assess applicants’ practical skills during hiring. Simulations Labs supports applicant assessment use cases so recruiters can screen candidates on real tasks.
- Universities and educators:
To teach applied cybersecurity and prepare students for careers. Academic programs use CTFs as engaging labs that build technical competence.
- Event organizers:
For community engagement and brand visibility. Organizers use CTFs to attract attendees and showcase expertise.
- Training providers and bootcamps:
To deliver hands-on labs at scale. Simulations Labs offers options for both on-demand and downloadable labs, supporting diverse teaching styles.
How to design an effective simulation or drill
Designing a useful exercise requires clear objectives and realistic scenarios. Follow these steps:
- Define goals: Are you measuring incident response time, technical skill, communication, or compliance readiness?
- Choose a format: tabletop for coordination, live attack for technical readiness, or CTF for skills training and assessment.
- Create realistic scenarios: model attacks relevant to your industry and tech stack (phishing, ransomware, supply-chain, web app exploitation).
- Set success criteria: determine KPIs such as Mean Time To Detect (MTTD), Mean Time To Respond (MTTR), or percentage of challenges completed.
- Run the exercise: simulate the attack and observe team behavior. Keep controllers to inject events and monitor progress.
- Debrief and iterate: conduct an after-action review, document lessons learned, and update playbooks and training plans.
How Simulations Labs simplifies running cyber drills and CTFs
Simulations Labs was built to remove the technical overhead of launching robust cybersecurity simulations. Key features that make it an effective platform:
- No-code authoring: create scenarios and challenges without writing infrastructure code.
- Custom content: upload your own labs with our no-code builder.
- Dynamic Flag Feature: assign unique flags to each participant to prevent flag sharing and cheating.
- Analytics & reports: export competition lists, participant reports, and leaderboards as CSV, Excel, or PDF for post-exercise analysis.
- Live leaderboard: engage participants and provide real-time performance visibility.
Explore product capabilities and see a demo on the Simulations Labs product demo page.
Measuring success: metrics to track
To prove value, track both technical and organizational metrics:
- MTTD and MTTR, faster detection and response indicate improved readiness.
- Challenge completion rates, measure skill levels and content difficulty.
- First solver stats and common failure points, identify knowledge gaps.
- Communication effectiveness, time to escalate, stakeholder notification times.
- Improvements between runs show progress across sessions.
Practical tips for starting small
If you’re new to simulations, begin with a focused pilot:
- Run a one-day exercise with a single scenario relevant to your most critical assets.
- Use pre-built content to save time and get baseline metrics quickly.
- Include non-technical stakeholders to test coordination and communication.
- Document lessons and scale complexity in future runs.
Conclusion: Make simulations part of your security program
Cyberattack simulations and cyber drills provide measurable benefits across people, process, and technology. They build practical skills, validate detection and response systems, and demonstrate readiness to stakeholders. Platforms like Simulations Labs make it straightforward to create, run, and measure these exercises with features tailored for CTF hosting, cybersecurity simulations, cyber drills, and cyber ranges.
To learn more, visit the Simulations Labs main website, explore our guides, or read recent blogs and case studies to see real-world examples.
Ready to try a simulation? Start hosting a CTF with Simulations Labs today: Host CTF Competition.